Introduction
In the age of cloud computing, security strategies must face constant change. Identity and access management are becoming more important than network security. An old paradigm is being superseded: for classical security concepts, network security was always the first line of defense.
Let’s take a look again at our old friend “network security”!
Old but Gold
“My mother used to say: the older you get, the better you get. Unless you’re a banana.” – Rose, Golden Girls
Network security may be an old approach to security, but it has evolved over the last few decades. Attacks on networks first emerged in the 1980s, with new technologies leading to the development of new security mechanisms. Procedures like ACL, encryption and encrypted protocols appeared on computer screens. Over the years, additional security layers were added to the network security portfolio. The new standard was the defense-in-depth concept, employing multiple layers of security controls to protect IT systems. The latest trend in network security is the zero-trust approach.
Most contemporary cyberattacks are launched from a “trusted” device. The zero-trust principle counteracts this attack vector. “Zero trust” means that no network device is trusted: each internal network device is viewed as a risk and must be restricted like a public network device.
Both approaches – defense in depth and zero trust – have to be adapted to the cloud!
New Technology – Old Problems
In on-premises infrastructures, network segmentation is provided by firewalls and VLAN segmentation within the network segments. But in the cloud, you cannot control the physical network layer and you cannot segment networks with VLAN. To solve this problem Azure provides a wide and diverse range of segmentation controls.
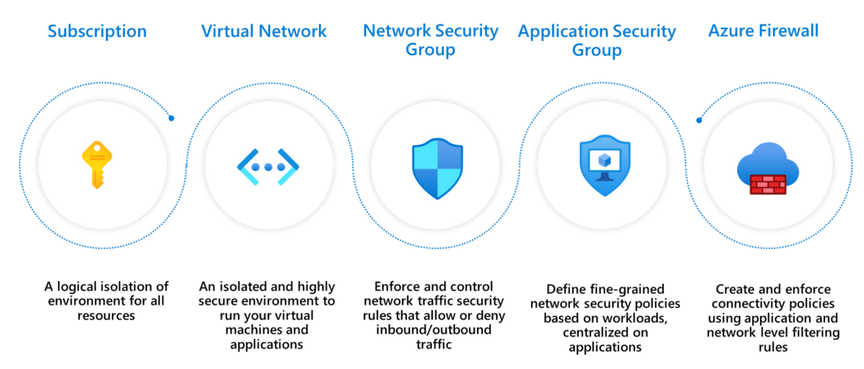
Source: Microsoft
Combining these controls yields a segmented and secured cloud environment. While subscription logically isolates all resources, network security groups (NSG) are stateful ACLs for traffic flowing in and out of a virtual network. The Azure Firewall forms the border to the World Wide Web and controls traffic from that wide world.
Segmentation Patterns for Azure Networks
Three common patterns provide different types of isolation and connectivity, depending on your infrastructure and organization.
Pattern 1: Single Virtual Network
This pattern applies to operation within single regions, since a virtual network cannot span multiple regions. All components of your workload then occur in one virtual network.
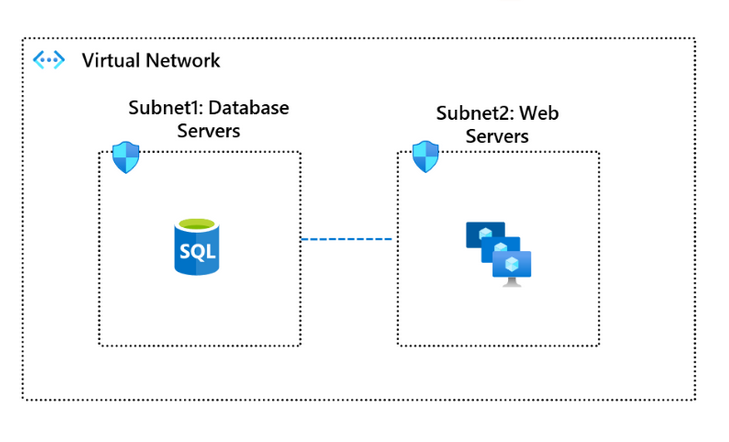
Source: Microsoft
The figure illustrates the segmentation of two subnets with NSGs. Subnet 1 contains the database, Subnet 2 the web servers. This constellation allows setting up NSGs so that only Subnet 2 can be reached through the internet. Subnet 1 can talk only with subnet 2.
The concept can be expanded to include more than these two subnets.
Pattern 2: Multiple Virtual Networks with Peering
Pattern 2 is an advancement on Pattern 1. Whereas Pattern 1 employs only one virtual network, Pattern 2 utilizes multiple virtual networks.
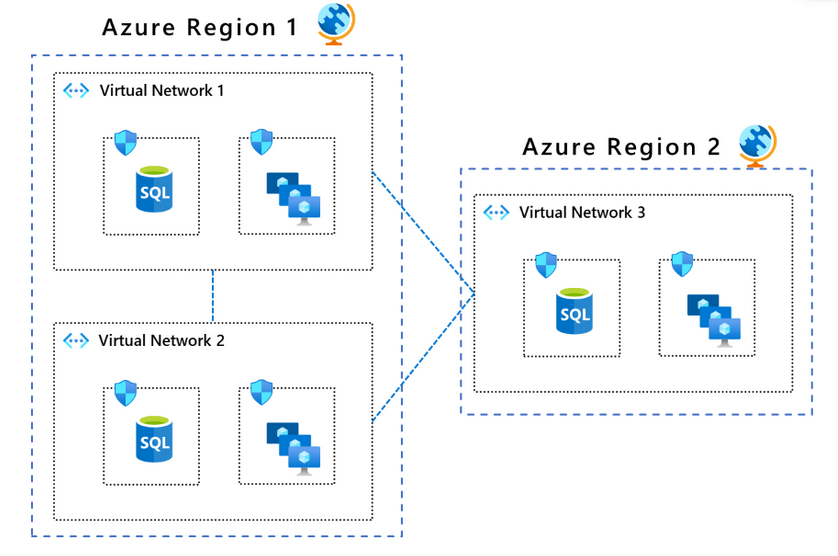
Source: Microsoft
In this concept, the integrated segmentation in virtual networks and the NSGs segment traffic in the virtual networks. The pattern can be used to peer different regions (or virtual networks). Each virtual network must be expressly peered to another virtual network.
Pattern 3: Multiple Virtual Networks with Hub-and-Spoke Model
The third pattern employs one virtual network (VNET) as a hub for communication with all other VNETs in the Azure Region. VNET peering connects Region 1 to Region 2.

Source: Microsoft
The biggest benefit of this pattern is that as your network grows, security activities do not expand, so that you can implement new networks and thereby avoid overhead costs related to security systems. The VNET hub requires a layer 3 router; you can choose the Azure Firewall or other virtual network appliance.
These three patterns are only recommendations; find your own combination of the patterns and underlying principles to attain your objective. The great thing about the cloud is the flexibility and tooling allowing you to develop your own design!
Segmentation with On-Premises and Azure Networks
After looking at cloud network partitioning, you may now ask: “How can I combine these approaches with my on-premises infrastructure?”. In most cases you want to connect your old networks to the new Azure networks. So let’s consider a reference architecture covering such a use case.
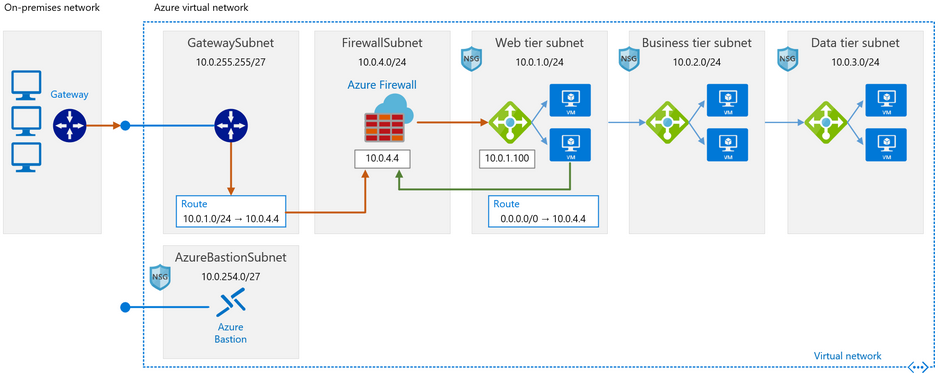
Source: Microsoft
The hybrid network reference architecture contains the following components:
- On-premises network
- Azure virtual network
- Gateways
- Azure Firewall
- Load balancer
- Virtual network routes
- Azure Bastion
This approach includes:
- Access control
- Network flow control
- Isolation and segmentation of networks
- Load balancing between virtual machines
The connection between your on-premises network and the Azure networks is implemented as an encrypted connection (such as VPN) between your on-premises gateway and the Azure gateway (in the gateway subnet). The virtual network routes compel all traffic to flow across the firewall. The firewall acts as a hub and relays the traffic to the desired destination (for security reasons, all traffic should pass through the firewall!). The load balancers receive the network traffic from the firewall and decide which machine has the resources to handle the traffic.
Azure Bastion is recommended for accessing Azure machines via SSH or RDP with a secure connection.
This reference architecture is just an example of how you can realize your objective. Adapt it to your needs and enjoy full control and security for your hybrid network!
Never too Old to Rock!
Network security may no longer be the first line of defense in cloud computing. To achieve a secure cloud environment, you need a combination of different security approaches. Apart from shared responsibilities, IAM and threat detection, network security is more indispensable than ever before! And after decades of evolving it is also in better shape than ever before!
The above concepts give you an idea of how to implement micro segmentation for your networks and how the underlying principles can support your own zero-trust approach. By adapting the concepts and combining the principles to meet your requirements, you’ll be able to create an optimally secure network.
Overhaul your old security concepts and enrich them with new ideas. Connect your networks to get the best from both generations!
Author: Dominic Iselt, IT Security Engineering Expert
